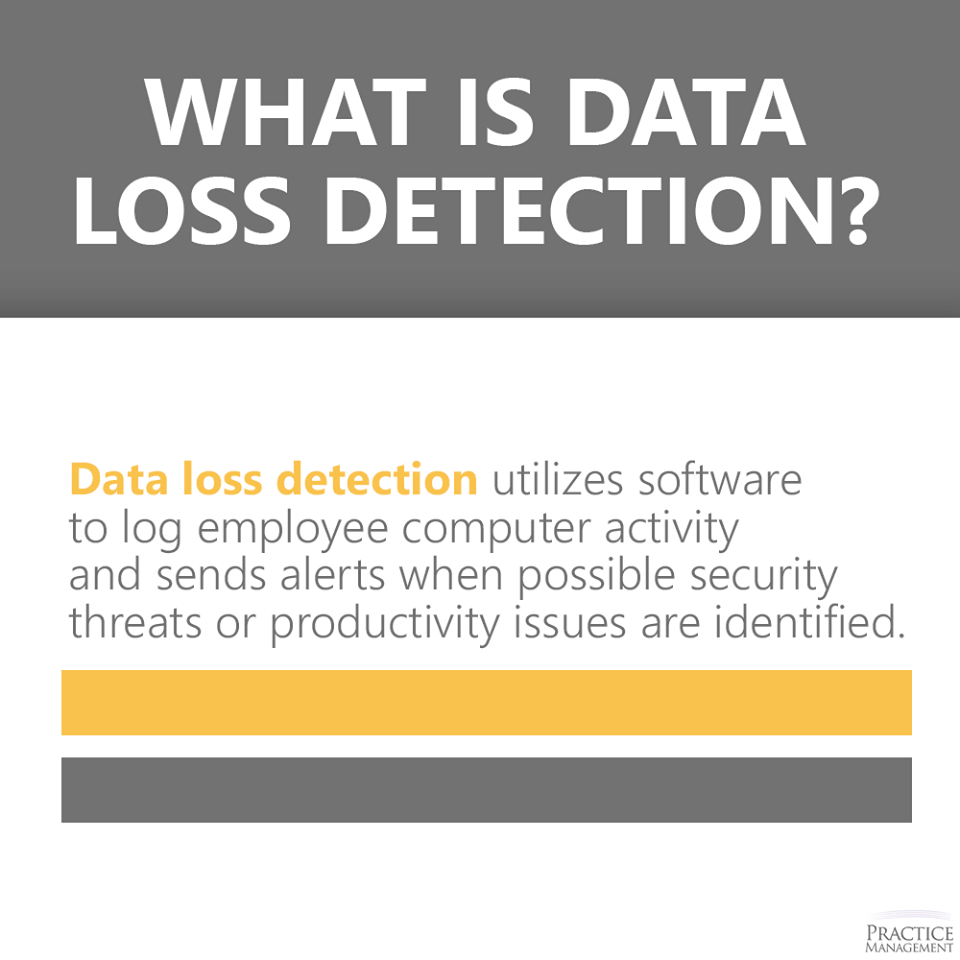
Having measures like data loss detection is vital when protecting health information. Without them it’s akin to leaving your front door open in an unsafe neighborhood. Eventually something is going to get stolen.

If your staff feels as if they are being pulled in one million directions at once, it’s probably a good time to investigate outsourcing some of your tasks.

At Practice Management we are extremely serious about securing Protected Health Information (PHI) and Electronic Protected Health Information (ePHI). That’s why we implement the most stringent safeguards.

All it takes is one weak point for a cyber criminal to breach your defenses and gather sensitive data from your files. One lapse from one employee can be extremely costly.

Another plus, you can stay up on reviews and respond to inquiries. Keeping up with your online reputation in our modern market is crucial.

